What is an exploit?
Exploits are written to take advantage of weaknesses (or vulnerabilities) in legitimate software. A project called Common Vulnerabilities and Exposures (CVE) gives each vulnerability a unique number, in this case "CVE-2012-4681".
About Exploit:Java/CVE-2012-4681
If you visit a website containing the malicious code while using a vulnerable version of Java, Exploit:Java/CVE-2012-4681 is loaded. It then attempts to download and run files from a remote host/URL. The files that are downloaded and run could be any of the hacker's choice and could include other malware.
This threat uses a software vulnerability to download and run other files on your PC, including malware.It runs when you visit a hacked website and you have a vulnerable version of Java. A number of legitimate websites could be hacked to unwillingly host this threat. The vulnerability that this threat exploits is described in CVE-2012-4681. This exploit targets the Java plug-in for web browsers. Java programs (or applets) can be used by websites and run in a "sandbox" – where the plug-in enforces rules on what the applet can do so that it cannot escape the restricted environment.
Exploit:Java/CVE-2012-4681 attacks the security model instead of memory corruption issues. With memory corruption issues, the exploit is dependent on the specific CPU (Central Processing Unit) type and operating systems, and might be affected by mitigation technology like DEP (Data Execution Prevention) or ASLR (Address Space Layout Randomization). Attacking the security model means that the exploit might be effective on any platform the Java interpreter is on; for example Windows, MacOS, Linux, etc. Usually the exploits are written using a few Java classes working together. The various class files are bundled into an archive called a JAR, which uses the ZIP file format. Every JAR contains a Manifest.MF file to identify itself to the Java Runtime. Since it is found in every JAR, it won't be listed.
Once Exploit:Java/CVE-2012-4681 gets into the computer, it will change the computer setting. When you start the computer, Exploit:Java/CVE-2012-4681 will run automatically at the background without any consent. To detect and remove this threat and other malicious software that may be installed on your computer, run a full-system scan with an appropriate, up-to-date, security solution. It is suggested to remove Exploit:Java/CVE-2012-4681 from the computer as soon as possible.To look deep into the threats, it is suggested to scan your computer with a anti-spyware like Spyhunter to find the detail problem.
How to remove Exploit:Java/CVE-2012-4681?
Manually remove Exploit:Java/CVE-2012-4681
Step 1: Press Ctrl+Alt+Del keys together and stop Exploit:Java/CVE-2012-4681 processes in the Windows Task Manager.
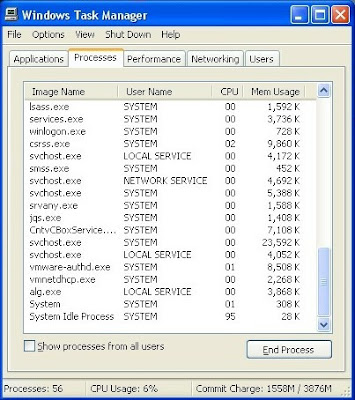
Step 2: Disable any suspicious startup items that are made by infections from Exploit:Java/CVE-2012-4681.
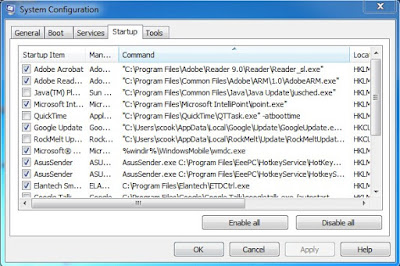
Step 3: Search the registry entries in your Registry Editor and then remove all of them.
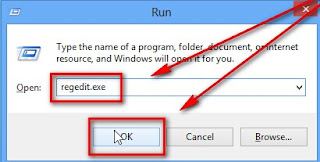
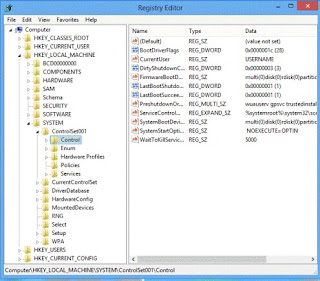
Automatically remove Exploit:Java/CVE-2012-4681
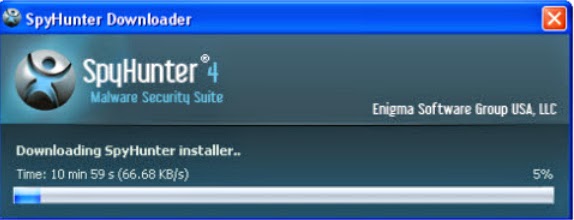
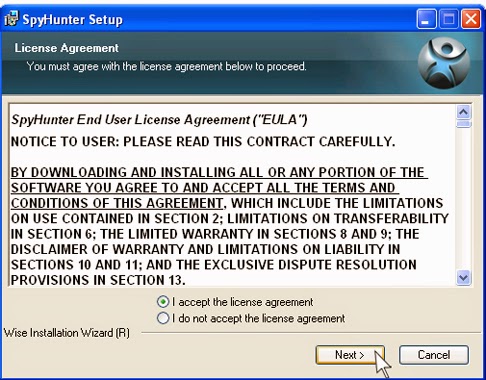
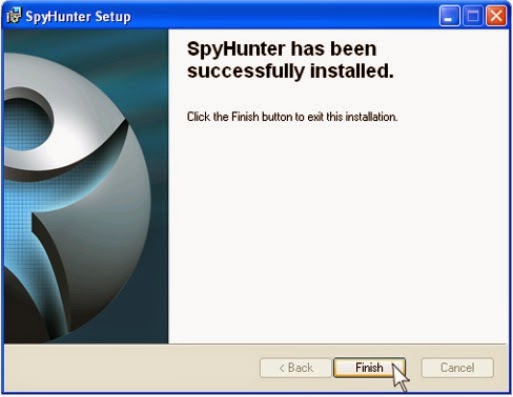.jpg)
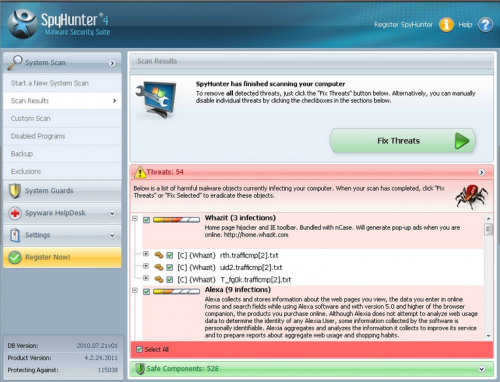
Step 3. Run SpyHunter to scan your PC.
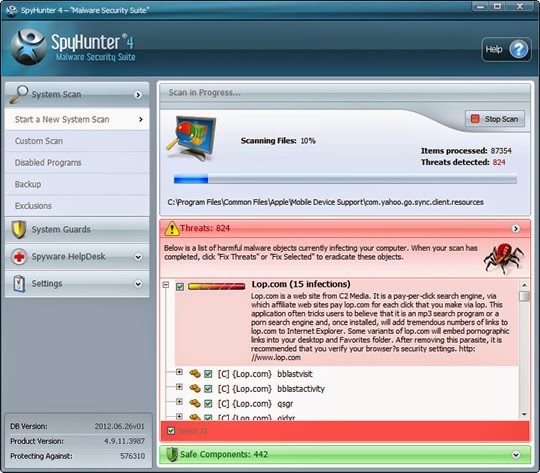
Step 4. Click on the Fix Threats to get all detected items deleted.
Summary
Exploit:Java/CVE-2012-4681 is a threat to your computer. To protect your computer from further damage, it is better to remove Exploit:Java/CVE-2012-4681 from the computer as soon as possible. To download Spyhunter to remove threats easily and safely now.
(Gary)
(Gary)

No comments:
Post a Comment