Infected with Exploit:Java/CVE-2010-4452
Exploit:Java/CVE-2010-4452 has become a nasty computer infection which attack many user's computer:
Exploit:Java/CVE-2010-4452 is the detection for an HTML file that exploits a vulnerability in Java described in CVE-2010-4452. This exploit uses a vulnerability in your software to infect your PC. It's usually used to install other malware or unwanted software without your knowledge. This threat is a webpage that spreads the exploit kit known as Neutrino.You PC is at risk of infection if you visit this webpage and you have vulnerable software installed on your PC. You might be redirected to the malicious webpage without your consent.
Exploit:Java/CVE-2010-4452 can slip into your computer by following means:
1. Malware developers often use tricks to pack the virus into the spam email attachment;
2. Many viruses spread by infecting removable drives such as USB flash drives or external hard drives.
3. Malware can be installed at the same time as other programs that you download.
4. Malware can come with Hacked or compromised webpages.
5. Some types of malware can download other threats to your PC.
Once Exploit:Java/CVE-2010-4452 gets into the computer, it will change the computer setting. When you start the computer, Exploit:Java/CVE-2010-4452 will run automatically at the background without any consent.Exploit:Java/CVE-2010-4452 can bring in other threats. It can connect to the Internet in order to request data and download files. To detect and remove this threat and other malicious software that may be installed on your computer, run a full-system scan with an appropriate, up-to-date, security solution. It is suggested to remove Exploit:Java/CVE-2010-4452 from the computer as soon as possible.To look deep into the threats, it is suggested to scan your computer with a anti-spyware like Spyhunter to find the detail problem.
Exploit:Java/CVE-2010-4452 can slip into your computer by following means:
1. Malware developers often use tricks to pack the virus into the spam email attachment;
2. Many viruses spread by infecting removable drives such as USB flash drives or external hard drives.
3. Malware can be installed at the same time as other programs that you download.
4. Malware can come with Hacked or compromised webpages.
5. Some types of malware can download other threats to your PC.
Once Exploit:Java/CVE-2010-4452 gets into the computer, it will change the computer setting. When you start the computer, Exploit:Java/CVE-2010-4452 will run automatically at the background without any consent.Exploit:Java/CVE-2010-4452 can bring in other threats. It can connect to the Internet in order to request data and download files. To detect and remove this threat and other malicious software that may be installed on your computer, run a full-system scan with an appropriate, up-to-date, security solution. It is suggested to remove Exploit:Java/CVE-2010-4452 from the computer as soon as possible.To look deep into the threats, it is suggested to scan your computer with a anti-spyware like Spyhunter to find the detail problem.
How to remove Exploit:Java/CVE-2010-4452?
Manually remove Exploit:Java/CVE-2010-4452
Step 1: Press Ctrl+Alt+Del keys together and stop Exploit:Java/CVE-2010-4452 processes in the Windows Task Manager.
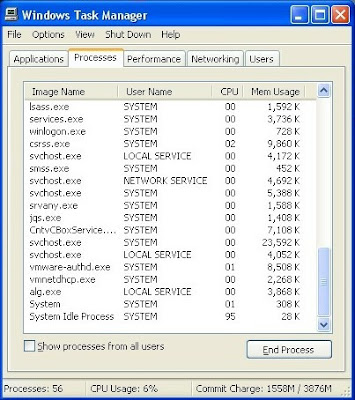
Step 2: Disable any suspicious startup items that are made by infections from Exploit:Java/CVE-2010-4452.
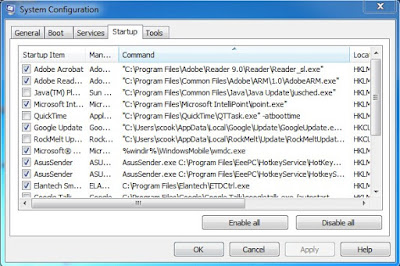
Step 3: Search the registry entries in your Registry Editor and then remove all of them.
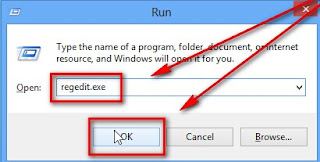
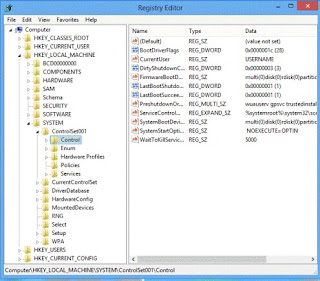
Automatically remove Exploit:Java/CVE-2010-4452
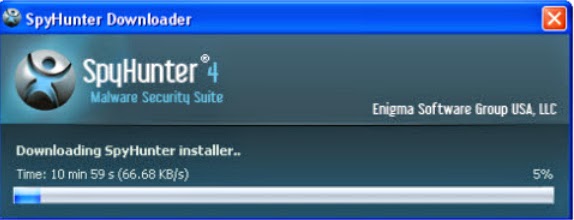
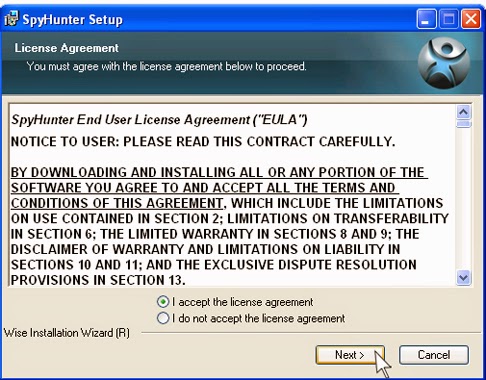
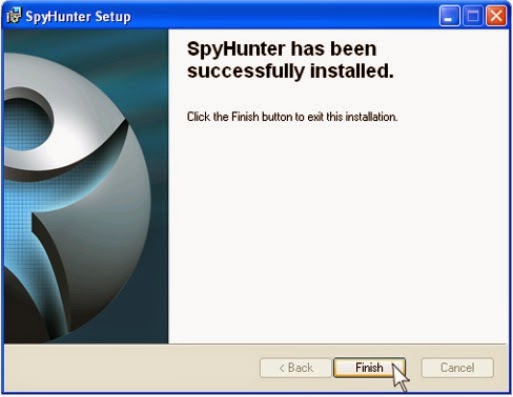.jpg)
Step 3. Run SpyHunter to scan your PC.
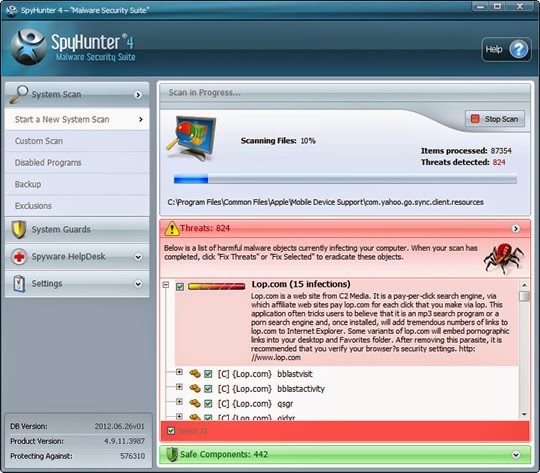
Step 4. Click on the Fix Threats to get all detected items deleted.
Summary
Exploit:Java/CVE-2010-4452 is a threat to your computer. To protect your computer from further damage, it is better to remove Exploit:Java/CVE-2010-4452 from the computer as soon as possible. To download Spyhunter to remove threats easily and safely now.
(Gary)
(Gary)

No comments:
Post a Comment