
What Is Fudx@lycos.com?
Fudx@lycos.com is one of the malicious ransomwares which is so evil that it should be remove immediately when it is found. Fudx@lycos.com can completely encrypt your confidential files, .jpg, .PDF, .doc, .xls etc. Cyber criminals design Fudx@lycos.com aiming to get money from computer users. If you think that cyber criminals will help you decrypt your files, you will be wrong. In most cases, even if users have given money to cyber criminals, these criminals will not bother themselves to decrypt your data since their purpose is money and they have gained it. Therefore, we strongly advice you don’t send any money to those notorious criminal if the data are not that important, and remember to back up your data from to time.What’s more, Many users are cheated by Fudx@lycos.com helps which promises users that they get back the damaged files after the payment. However, Fudx@lycos.com just install more and more malware on the background silently. Fudx@lycos.com aims to encrypt the whole personal files and the system files as well. Therefore, never hesitate to remove Fudx@lycos.com as soon as possible once it is found on your computer.
If you are unlucky to be one of the victims of Fudx@lycos.com, we never advise you to send one bitcoin to get back your files. If you do so, you may lose your files and money at the same time.You are strongly advisable to get rid of Fudx@lycos.com completely before it cause serious problems.
How to remove Fudx@lycos.comr effectively?
Solution 1: Manually remove it yourself by following the guides below.
Solution 2: Automatically remove it by using SpyHunter.
Solution 1: Manually Removal Guide
There is a video for manually helping you remove ransomware Fudx@lycos.com.
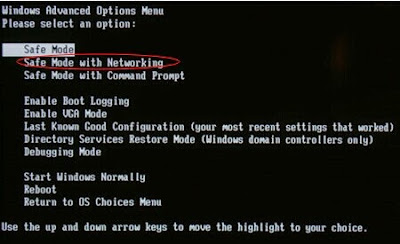
Step 1:Enter Safe Mode.
To achieve a better result, you should enter Safe Mode first. Start up your PC and keep pressing F8 keys before it launches Windows. And then choose "Safe Mode with Networking". If you're not allowed to access to your screen, choose Safe Mode with Command Prompt.
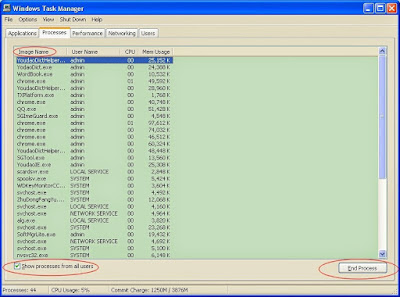
Step 2: End the processes of related ongoing programs.
Use Ctrl+Shift+Esc keys to help you. You can quickly find the processes tab. Select all related or suspicious programs and then end them.
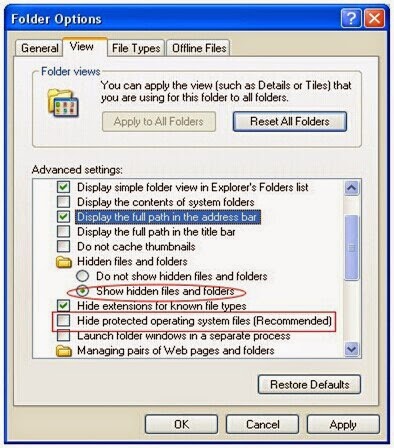
Step 3: Show hidden files and folders.
Click start menu to find Control Panel. Focus on “Appearance and Themes” to get to Folder Options. In View tab, tick “Show hidden files, folders” and deselect “Hide protected operating system files (Recommended), and then confirm your actions.
Step 4: Delete all related or suspicious files.
Since all the hidden files have been shown, you can delete them right now!
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpCmdRun.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpUXSrv.exe
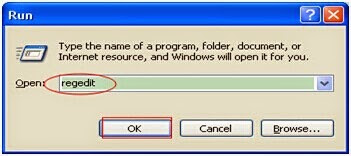
Step 5: Remove registry entries.
Click start and find Run. Type "regedit" into the pop-up box and then you can see the Registry Editor. Choose all related or suspicious registries and remove them.
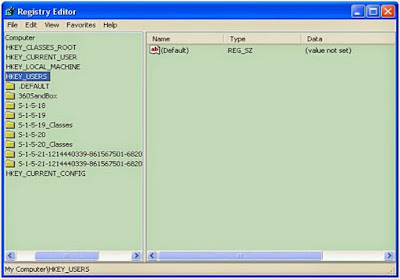
Solution 2: Automatically Removal Guide
If you choose to remove Fudx@lycos.comr automatically by using SpyHunter, your choice may be the most welcomed way of doing so. For you don't have to worry about the mistaken delete files and you can save your time and energy.
Step 1: Download SpyHunter, and follow the installation guides to install it properly.
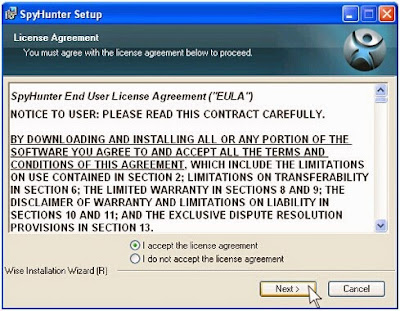
Step 2: After you install SpyHunter, run it to scan your whole system.
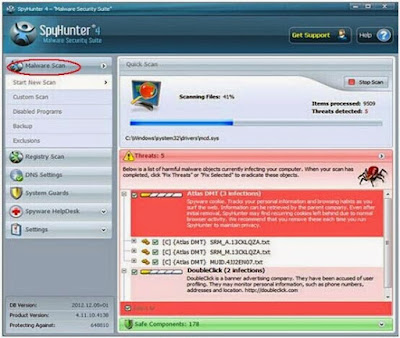
Step 3: After the scan is over, select all the threats and click "Remove" to fix all the threats.
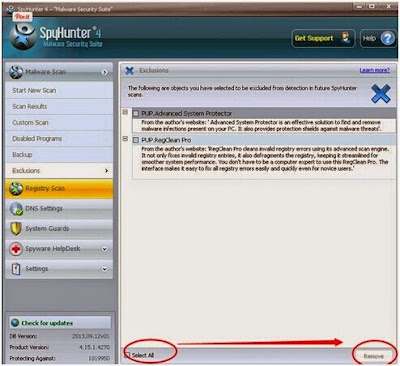
Fudx@lycos.comr is a new ransomware(ransom Trojan) which is able to encrypt your files.Never give money to get back your files.If you do so, you may lose your files and money at the same time. You are strongly advisable to get rid of Fudx@lycos.com completely with SpyHunter. SpyHunter is a powerful, real-time anti-spyware application which can assist the average computer user in protecting their PC from malicious threats. As malware continues to evolve and become more sophisticated, SpyHunter can effectively protect the average computer users’ computer from malware threats.


No comments:
Post a Comment